A cryptocurrency wallet is a piece of software that keeps track of the secret keys used to digitally sign cryptocurrency transactions for distributed ledgers. Because those keys are the only way to prove ownership of digital assets – and to execute transactions that transfer them or change them in some way – they are a critical piece of the cryptocurrency ecosystem.
Better known as "crypto wallets," they are like the keys to the blockchain car. Without those keys, the car won't run. And without them, there would be no way to prove ownership of a digital asset - anything from a bitcoin to a token representing some kind of asset.
What a crypto wallet does
Not only does a crypto wallet (or more generically, a digital wallet) keep track of encryption keys used to digitally sign transactions, it also stores the address on a blockchain where a particular asset resides. If the owner loses that address, they essentially lose control over their digital money or other asset, according to David Huseby, security maven for the Linux Foundation's Hyperledger Project.
 Coinbase
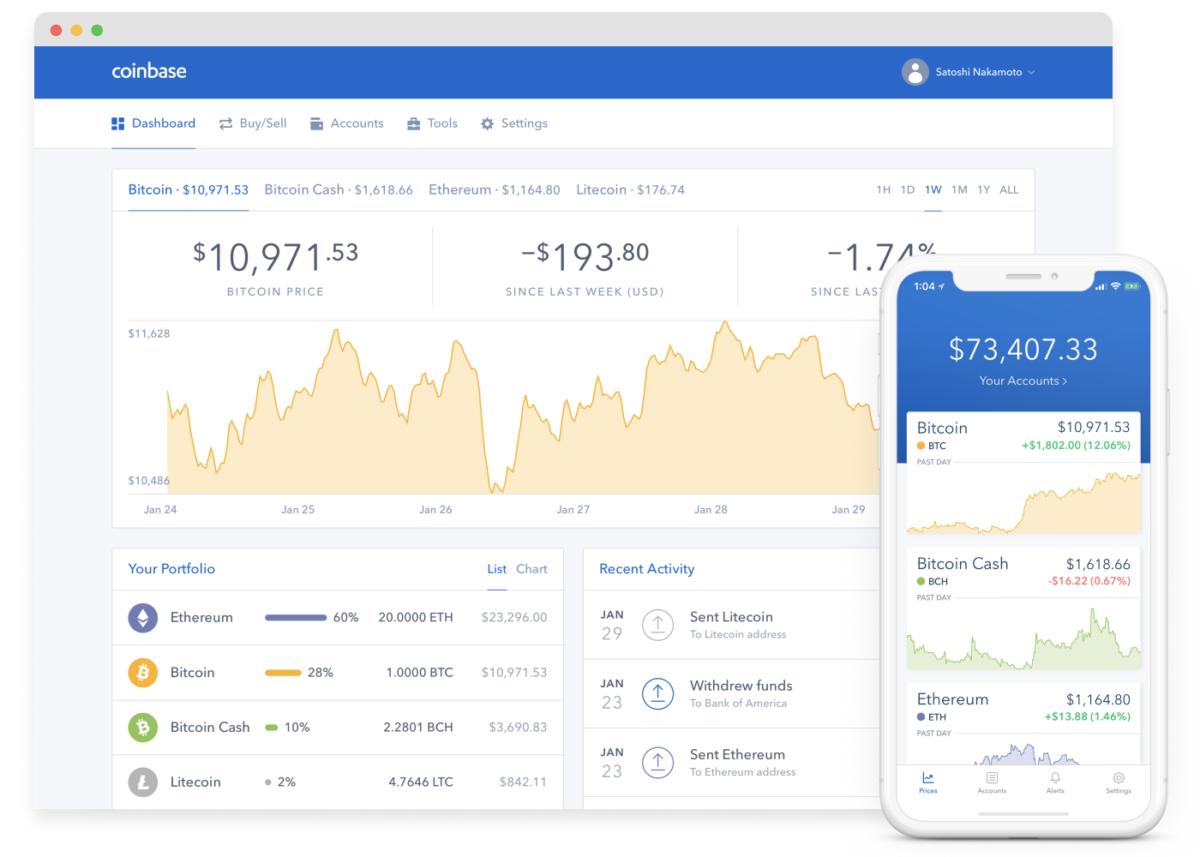
Coinbase
Coinbase's crypto wallet user interface.
There are two main types of crypto wallets: hardware and software (also known as cold and hot storage wallets, respectively). Hot storage wallets are accessible via an internet service such as Coinbase, one of the largest cryptocurrency exchanges that supplies online wallets for users, and can be further segregated into online wallets and client-side wallets managed locally on a user's computer or mobile device.
There are also paper wallet generators, which create keys that can be printed out or rendered as QR codes.
Cold storage wallets are downloaded and reside offline on a piece of hardware such as a USB drive or a smartphone. Exodus.io and Dash QT are two examples of cold storage wallet software. Cold storage wallets can also be purchased as devices with the software already installed on them; these kinds of devices are sold by vendors such as Trezor and Ledger.
Hardware wallets can be further divided into crypto-assist type wallets that simply handle the keys and signing of arbitrary data and are sometimes called hardware security modules (HSMs). "And then there are hardware wallets that handle generating and signing complete transactions that are then sent to the distributed ledger network," Huseby said.
 Trazor
Trazor
Trazor's USB-based cold storage dongle.
When you communicate with the blockchain, the hardware communicates through the codes on the device. It's not a very friendly user interface, though, according to Gartner Vice President of Research Avivah Litan.
Hot and cold wallets – which is more secure?
A cold storage wallet is innately more secure than a hot wallet because it's not connected to the internet. Most cryptocurrency attacks have occurred when a hacker hits an online wallet service and transfers the secret keys to their own wallet – essentially transferring the associated funds, as well, according to Litan.
In 2014, for example, the Japanese online crypto exchange Mt. Gox suffered the theft from its hot wallet of 850,000 bitcoins valued at more than $450 million. And in 2018, bitcoin exchange service Coincheck suffered a theft of almost $1 billion worth of cryptocurrency from its hot wallet service. Many smaller thefts have taken place over the past five years, mostly through the hacks of online wallets.
"One of the commonest attack vectors used to steal funds from blockchain cryptocurrency accounts is [a] takeover of customer accounts. This is the primary reason we recommend not storing any cryptocurrency balances in online wallets," Litan wrote in a research note earlier this year.
How to bolster crypto wallet security
Gartner recommends converting cryptocurrency into fiat money – cold hard cash, as in real dollars, Euros, Yen or some other currency – for safe-keeping, or storing crypto keys in a cold wallet. The latter then means making a paper copy of the keys and storing that paper in a secure place such as a bank safety deposit box.
Paper can also be used as a type of wallet through software that creates a QR code that can be scanned to enable blockchain transactions. Otherwise, Gartner recommends the use an online exchange with a wallet service that enforces two-factor authentication through push technology. Push technology binds the second factor to a registered mobile phone, so that only an owner's phone can approve an access request pushed out by the exchange wallet's authentication service.
Centralized wallet services have been lucrative targets in the past because hackers could make off with millions of dollars' worth of cryptocurrency in just a few minutes. But cryptocurrency hackers have also successfully stolen the SIM identity of a mobile phone with a phone-based wallet on it, according to Huseby.
It's important to recognize that determined criminals can circumvent most phone authentication techniques using a variety of methods, according to Gartner. These include "SIM swaps," where a thief registers an existing number to his or her phone, so that push notifications or messages are sent to that phone, instead of to the legitimate owner. Hackers do this typically through social engineering of mobile phone customer service representatives, Gartner's report said.
There have also been thefts of cryptocurrency via malware planted onto a cryptocurrency owner's device, allowing their secret keys to be stolen.
"There are ways to mitigate all of these attacks, but the best solution so far is to use some kind of hardware wallet and also to have a hard copy backup of your secret keys somewhere safe," Huseby said. "The hardest part of wallets is that they are responsible for secure storage of small, highly sensitive data. Most people are not familiar with the levels of security and paranoia that is required to truly defend against people determined to steal your keys."
 Ledger
Ledger
Ledger's Nano S USB-type cold storage crypto wallet.
The danger of lost keys
The main problem with a cold wallet, however, is if you haven't backed up the information on it or stored a hard copy of it somewhere secure – and you lose that device – you lose your digital assets for good. Simply put, you no longer know where your cryptocurrency resides on a blockchain or have the keys to authenticate that you are the owner.
Hot storage wallets, in contrast, have the benefit of service provider support. If you lose your access code to the wallet, there are challenge-and-answer questions that will allow you to recover them.
Conversely, there are limited methods for recovering private keys in a cold storage wallet that has been lost, and they are generally not easy to use. For example, Coinbase allows users a restore mechanism that consists of 24 random word recovery phrase users are supposed to record when they create their wallet.
Blockchain ledgers work based on a trustless consensus mechanism, meaning you don't need to know the person or people you're transacting with on the ledger. A distributed ledger will trust any transaction properly signed by a valid secret key. That's why protecting keys is so important.
"Wallets serve the purpose of storing those keys securely and doing the digital signing necessary for the distributed ledger to accept the transaction," Huseby said.
Beyond digital currency: other uses for crypto wallets
While the vast majority of crypto wallet applications are used to store cryptocurrencies such as bitcoin, Ethereum, Ripple or Litecoin, the software can also store the keys to fungible and non-fungible digital tokens representing goods, financial assets, securities, and services.
For example, a token stored in a crypto wallet could represent concert or plane tickets, unique artwork or goods in a supply chain – virtually anything with a digital value attached to it.
All distributed ledgers with decentralized consensus mechanisms rely on the capability security model, which means possession of an encryption key – proven with a digital signature over a transaction – authorizes the action the transaction represents.
"So any application modeled on a distributed ledger requires users to have wallets that they use to sign transactions that work for that application," Huseby said. For Bitcoin, the transactions just transfer bitcoins to another encryption key and therefore to another owner. For things like a supply chain, they sign transactions that track the asset being managed (e.g., electronic parts, raw materials, etc)."
In the future, a new, "trustless" global economy could be based on blockchain and crypto wallets that enable everything from individual financial or professional histories, tax information, medical information, or consumer preferences to corporations maintaining employee or partner digital identities and controlling application access.
Digitized representations of traditional identity documents such as driver's licenses, passports, birth certificates, Social Security/Medicare cards, voter registration info and voting records could also be stored in crypto wallets, giving owners control over who has access.
And making those crypto wallets even more valuable, and making it even more important that they be secure.






